Achieving Privacy and Security in the IT World (WK 1&2)
Tl;DR: In order to
have privacy and security in the IT world, it is important not to compromise one
for the other. This can be achieved by properly implementing security measures to
ensure that both privacy and security are being maintained.
Privacy and
security are two essential needs that almost everyone wants, and it can be
expressed in many different ways . It’s
the reason that we lock the front door to our home at night in order to feel
secure and protected. It’s the reason that we close our window blinds in order
to have a level of privacy in our homes. When a person is in their home, they
want a certain level security and privacy. Individuals also
require privacy and security for their personal information as well.
When it
comes to personal information, individuals want to make sure that their
information is secure and private. Often these two words can be used
interchangeable without an individual understanding the difference between the
two. But what exactly is the difference between privacy and security? And is it
possible to have both equally or must we sacrifice one for the other?
To better
understand the difference between privacy and security, it is important to
define exactly what each one means. To do that, we will look at
Merriam-Websters dictionary to define each word. Privacy is defined by
Merriam-Websters dictionary as freedom from unauthorized intrusion. Security is
defined by Merriam-Websters dictionary as freedom from danger. When we talk
about privacy and security, we are addressing the need for individuals to have
freedom from intrusions (Privacy) and freedom from danger (Security). But how are these two concepts applied in the IT world to
achieve privacy and security? That is what we will be examining in this blog
post.
In the IT
world of cybersecurity, these two words receive a lot focus due to what they
are applied to. When discussing privacy and security in the IT world, an
individual is focused on securing data and the privacy of the data owner. This
can be done through many different security measures and approaches, such
as restricting access by implementing two-factor authentication, installing
firewalls, intrusion detection systems, data encryption, and security
training. These measures can be applied in many different ways to secure
data and the privacy of the data owner.
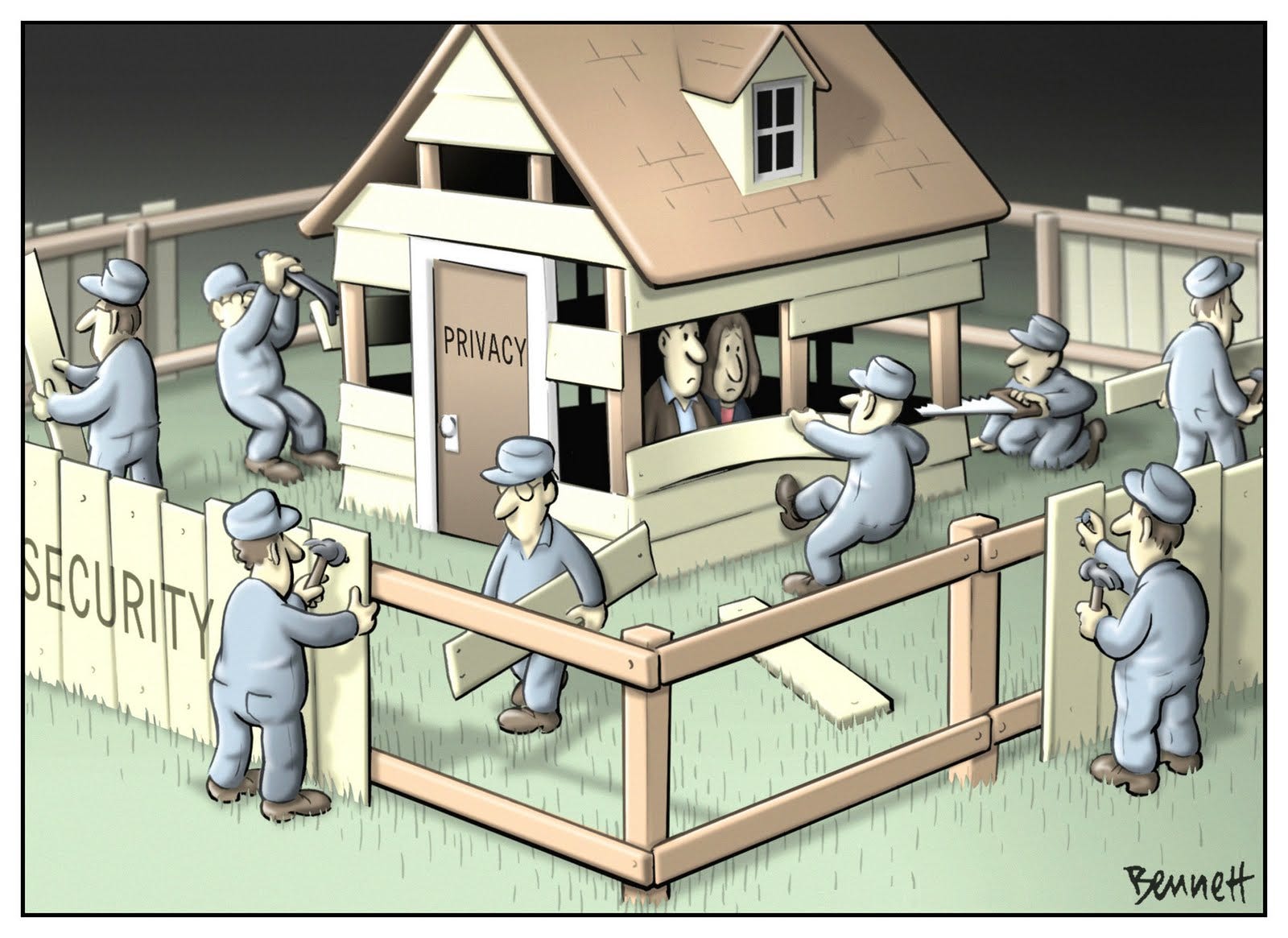
One
interesting question that has been raised in regard to privacy and security, is
can you have one without having the other? Or to
put it another way, does security require privacy and vice versa? This topic
has been highly debated with some arguing that both can be obtained while
others argue that you cannot have equal parts of both. But I believe the answer
to this question is easy to answer once the process of privacy and security is
closely examined.
In order to
have privacy, access must be restricted. If access must be restricted, then
security controls must be in place to restrict access. The two are interdependent
on each other in order to supply the desired outcome of privacy and security.
This is why a sacrifice in one can lead to a lessening in the other.
Take cloud storage as
an example, the user can upload their personal documents to their cloud account
where the data is stored. In order to secure the data, the cloud provider can
separate the data into pieces and encrypt each piece and store each piece on a
different server. This is done to secure the data and keep the data private.
The user’s password is the key to retrieve and decrypt the data that is stored
in the cloud and without it, the data cannot be accessed. This is one example
of security and privacy being offered without sacrificing one or the other.
In recent years
though, security has become a source of a lot of discussion. It has been put
forth by some that in order to have security, a certain level of privacy must
be sacrificed. Some might argue that for the benefit of national security an
individual may need to surrender some privacy. Others argue
that surrendering any level of privacy makes the individual less secure. No
matter what you think of him personally, one of Edwin Snowden’s more famous
quotes rings true on this topic. "Arguing that you don’t care aboutprivacy because you have nothing to hide is like arguing that you don’t careabout free speech because you have nothing to say”. I couldn’t
have said it better myself.
Essentially,
security and privacy are two sides of the same coin. They both must be implemented
in order to have one or the other. If a person wants privacy in their home and
they close their window blinds without locking their door, they have sacrificed
both. By not locking their front door, anyone can just walk in and their
privacy and security has been violated. If the person wants security and all
they do is lock their door and do not close their blinds, then anyone can just
look in the window. These simple analogies show how the two work together and
how they are dependent on one another.
In order to achieve
privacy and security in the IT world, the privacy of the individual must be
upheld while protecting and securing their data. This can be achieved if the
measures are put in place to not only protect the data from malicious actors,
but also from those who store the data also. When this balance is achieved by
implementing certain IT security measures, then both privacy and security can
be achieved for the individual.


Comments
Post a Comment